| File | Description |
|---|---|
/etc/ssh/moduli | Contains Diffie-Hellman groups used for the Diffie-Hellman key exchange which is critical for constructing a secure transport layer. When keys are exchanged at the beginning of an SSH session, a shared, secret value is created which cannot be determined by either party alone. This value is then used to provide host authentication. |
/etc/ssh/ssh_config | The default SSH client configuration file. Note that it is overridden by ~/.ssh/config if it exists. |
/etc/ssh/sshd_config | The configuration file for the sshd daemon. |
/etc/ssh/ssh_host_ecdsa_key | The ECDSA private key used by the sshd daemon. |
/etc/ssh/ssh_host_ecdsa_key.pub | The ECDSA public key used by the sshd daemon. |
/etc/ssh/ssh_host_key | The RSA private key used by the sshd daemon for version 1 of the SSH protocol. |
/etc/ssh/ssh_host_key.pub | The RSA public key used by the sshd daemon for version 1 of the SSH protocol. |
/etc/ssh/ssh_host_rsa_key | The RSA private key used by the sshd daemon for version 2 of the SSH protocol. |
/etc/ssh/ssh_host_rsa_key.pub | The RSA public key used by the sshd daemon for version 2 of the SSH protocol. |
/etc/pam.d/sshd | The PAM configuration file for the sshd daemon. |
/etc/sysconfig/sshd | Configuration file for the sshd service. |
Applies to Windows Server 2019, Windows 10
OpenSSH version 8.2 added support for FIDO U2F hardware authenticators. FIDO devices are supported by the public key types “ecdsa-sk” and “ed25519-sk', along with corresponding certificate types. The alternative to OpenSSH 8.2 isn't Telnet but a second,older, copy of ssh under a different name. Keeping an extra copy of ssh around might require a bit of work but is better to require people to do extra work to be insecure than requiring extra work to be secure. If you want to you can even rename the older ssh binary to telnet.
OpenSSH 8.2 was released on 2020-02-14. Mirrors listed at OpenSSH is a 100% complete SSH protocol 2.0 implementation and includes sftp client and server support. Once again, we would like to thank the OpenSSH community for their continued support of the project, especially those who contributed. Crypto-policies is a component in Red Hat Enterprise Linux 8, which configures the core cryptographic subsystems, covering the TLS, IPsec, DNSSEC, Kerberos protocols, and the OpenSSH suite. It provides a small set of policies, which the administrator can select using the update-crypto-policies command.
OpenSSH is a connectivity tool for remote login that uses the SSH protocol. It encrypts all traffic between client and server to eliminate eavesdropping, connection hijacking, and other attacks.
OpenSSH can be used to connect Window 10 clients to Windows Server 2019. OpenSSH Client is available to install on Windows 10 build 1809 and later, while OpenSSH Server is available to install on Windows Server 2019 and later.
Openssh 8.2
Important
If you downloaded OpenSSH from the GitHub repo at PowerShell/openssh-portable, follow the instructions listed there, not the ones in this article.
Install OpenSSH using Windows Settings
Both OpenSSH components can be installed using Windows Settings. OpenSSH Server is installed on Windows Server and OpenSSH Client is installed on Windows 10 devices.
To install the OpenSSH components:
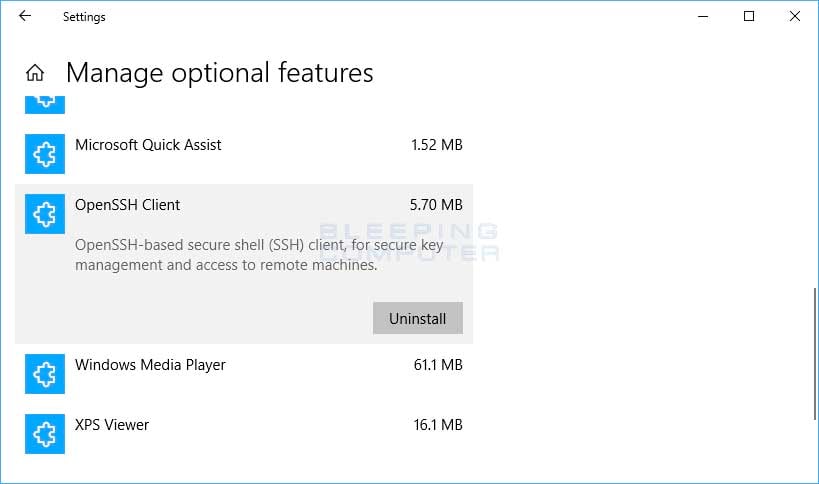
Open Settings, select Apps > Apps & Features, then select Optional Features.
Scan the list to see if the OpenSSH is already installed. If not, at the top of the page, select Add a feature, then:
- On Windows 10, find OpenSSH Client, then click Install
- On Windows Server 2019, find OpenSSH Server, then click Install
Once setup completes, return to Apps > Apps & Features and Optional Features and you should see OpenSSH listed.
Note
Installing OpenSSH Server will create and enable a firewall rule named OpenSSH-Server-In-TCP. This allows inbound SSH traffic on port 22. If this rule is not enabled and this port is not open, connections will be refused or reset.
Install OpenSSH using PowerShell
To install OpenSSH using PowerShell, run PowerShell as an Administrator.To make sure that OpenSSH is available, run the following cmdlet:
This should return the following output:
Then, install the server or client components as needed:
Both of these should return the following output:
Start and configure SSH Server
To start and configure OpenSSH server for initial use, open PowerShell as an administrator, then run the following commands to start the SSHD service:
Connect to SSH Server
Once installed, you can connect to OpenSSH Server from a Windows 10 device with the SSH client installed using PowerShell as follows. Be sure to run PowerShell as an administrator:
Once connected, you get a message similar to the following:
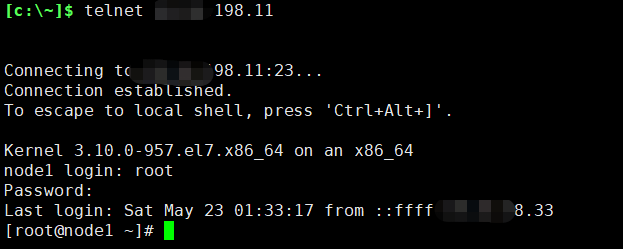
Selecting yes adds that server to the list of known ssh hosts on your Windows client.
You are prompted for the password at this point. As a security precaution, your password will not be displayed as you type.
Once connected, you will see the Windows command shell prompt:
Openssh 8.2p1
Uninstall OpenSSH using Windows Settings

Openssh 8.2p1
To uninstall OpenSSH using Windows Settings:
- Open Settings, then go to Apps > Apps & Features.
- Go to Optional Features.
- In the list, select OpenSSH Client or OpenSSH Server.
- Select Uninstall.
Uninstall OpenSSH using PowerShell

To uninstall the OpenSSH components using PowerShell, use the following commands:
Openssh Portable Windows
You may need to restart Windows afterwards if the service was in use at the time it was uninstalled.

Comments are closed.